Copyright @ 2025 Global Cyber Alliance | Sitemap

With the continuous progression of the importance of the Internet in our daily lives and the global pandemic having forced many businesses to seek an online presence, security is a major consideration and more important than ever. The vast majority of businesses now handle stock, customer information, and employee data online, and with HR and marketing departments all needing access, this means multiple user accounts and multiple logins. A 2019 security survey conducted by Google showed that a shocking 65% of people utilise the same passwords for multiple accounts and services. It is a common tactic used by cyber criminals across the globe – once they retrieve one password, they then try to find other accounts under the same name and use either the identical password or variations of it to try and brute force their way in.
There is a quick and easy way to mitigate against such attacks: use a different password for everything!
This would result in a separate password for online banking, every social media account, work accounts, personal email accounts, online shopping…the list goes on! Following a survey by NordPASS, the average person has approximately 100 passwords – which is almost impossible to remember. But here is an example of why using a different password for every account is so important: He spent 24 years building his business. A ransomware attack blew it to smithereens.
When creating an account, the user is often prompted to create a strong password using the following guidelines:
-
- At least 1 numeric character
- At least 1 capital letter
- At least 1 special character
- Must be longer than 8 characters
This often gives a result quite closely resembling gibberish – Gdjeh25!fh for instance would fit the guidelines! In particular, Apple has started suggesting strong passwords of their creation whenever the user is in a field that it has identified as password entry. As you can see, this password is a complete mix of letters and numbers, rendering it very hard to remember.
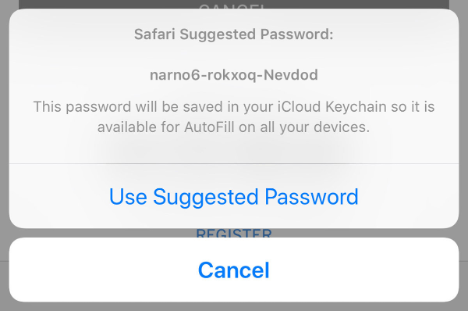
Apple uses a nifty piece of software called the iCloud Keychain to store all these strong gibberish passwords, meaning neither the user nor the phone needs to remember them. The keychain itself is very secure, using optional (but recommended) two factor authentication, having its own security code that must be used to access the stored passwords, and if the keychain account is set up on another device, the account owner must approve it first.
Password management software has become a necessity in the modern world to heighten business security, much like iCloud Keychain, which is free on all iOS devices. There are plenty available (both free and paid), however the toolkit contains Bitwarden, which is available on both mobile and desktop via browser add-ons and an app. It stores every password and every account, checks for security breaches on those sites and allows for auto-fill authentication, with one tap you can log into any account. No need to remember pesky passwords anymore!
The author Julia L is an NCSC CyberFirst University Bursary Student, she spent her eight-week 2021 summer placement with GCA
