
How to Recover from Password Exposure
This free guide that contains steps for recovering from such incidents where your password may have been exposed. It highlights...

This free guide that contains steps for recovering from such incidents where your password may have been exposed. It highlights...

The Blueprint for Ransomware Defense is a set of actionable and achievable Safeguards aimed at small- and medium-sized enterprises...

Should I use a browser-based password manager? Many web browsers now come with password managers built in, and they can be...
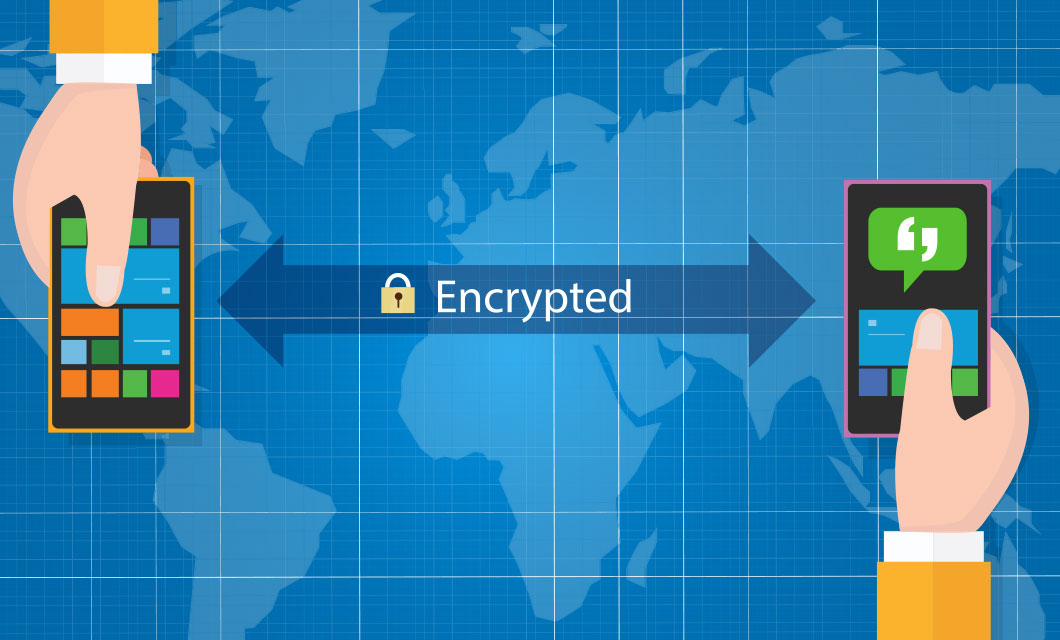
Email encryption is the process of disguising the content of your email messages to protect them from being read by unwanted...

This resource provides an overview of virtual private networks (VPNs) including how they work, what kinds of protection they...

Download the attached PDF to find out what email domain spoofing is and how DMARC can help protect against the malicious...

Download the attached PDF to find out what ransomware is and why it’s important to back up your data.

Download the attached PDF to find out why it’s important to use real time Anti-Virus and DNS filtering.
“Time” defines the approximate time it will take to implement the tool, including installation and setup. Based on your system and experience, the time may be longer or shorter than the time estimated.
Requires minimal technical knowledge to complete setup. Users with little-to-no familiarity with computer systems will still easily be able to implement Level 1 tools.
Requires basic technical understanding of operating systems and settings controls. Users with a basic understanding will be able to easily implement Level 2 tools.
Requires an intermediate level of understanding to implement. Users will need an intermediate understanding of computer systems and code languages.
Requires advanced levels of understanding of computer systems, settings and code languages. Users will need experience with advanced system configurations.
Contact Us
[email protected]
Community Forum
https://community.globalcyberalliance.org/